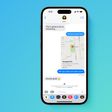
A new bug facing the iOS Mail app was found recently by security specialist Jan Soucek (via The Register). The malicious bug is capable of delivering false iCloud log-in prompts by allowing remote HTML content to be loaded through an email message delivered to the intended victim. The bug then delivers a convincing iCloud log-in box for users to re-enter their Apple ID and password. Soucek says that Apple did not respond to his discovery of the bug when he stumbled across it back in January.
"Back in January 2015 I stumbled upon a bug in iOS's mail client, resulting in HTML tag in e-mail messages not being ignored. This bug allows remote HTML content to be loaded, replacing the content of the original e-mail message. JavaScript is disabled in this UIWebView, but it is still possible to build a functional password "collector" using simple HTML and CSS."
The bug isn't relegated to only iCloud phishing attacks, however, letting anyone with access to it customize the attack to ask for whichever username and password credentials they feel the need for. Soucek kept the details of the bug only between himself and Apple, letting the company have time to possibly fix the attack and inform him of its progress. Given the company's remaining quietness on the subject, he decided to publish the proof of concept - called the Mail.app inject kit - on GitHub in hopes of spreading its awareness.
"It was filed under Radar #19479280 back in January, but the fix was not delivered in any of the iOS updates following 8.1.2. Therefore I decided to publish the proof of concept code here."
While Soucek's actions bring the malicious bug to more people's attentions and can help stop it in due time, it also means there's a wider chance for phishers to deploy it on their own. Until Apple comments on the story and offers a fix for the bug, it'll be safest to take precaution when any password prompt emerges while browsing email in iOS.



















Top Rated Comments
And then there's that.